Overview
Access tokens are the foundation of secure API authentication in Opigno Enterprise. The Access Token Management interface allows administrators to create, monitor, and control API access for external integrations like Zapier.Each access token is bound to a specific learning area and provides OAuth2-based authentication for API operations within that scope.
Accessing Token Management
To manage access tokens in your Opigno Enterprise instance:Navigate to Authentication Settings
- Log into your Opigno Enterprise backoffice as an administrator
- Locate the Configuration section in the left sidebar
- Click on Authentication
- Select Manage access tokens
Understanding the Token List
The Access Tokens page displays all active and expired tokens in your system. For each token, you can view:Token Information Displayed
The descriptive label assigned to this token for easy identification.
The unique OAuth2 client identifier used for authentication requests.
The date when this token will expire and can no longer be used for API access.
Available operations for this token, including:
- Revoke: Immediately invalidate the token
- Edit: Modify token settings (name, expiration)
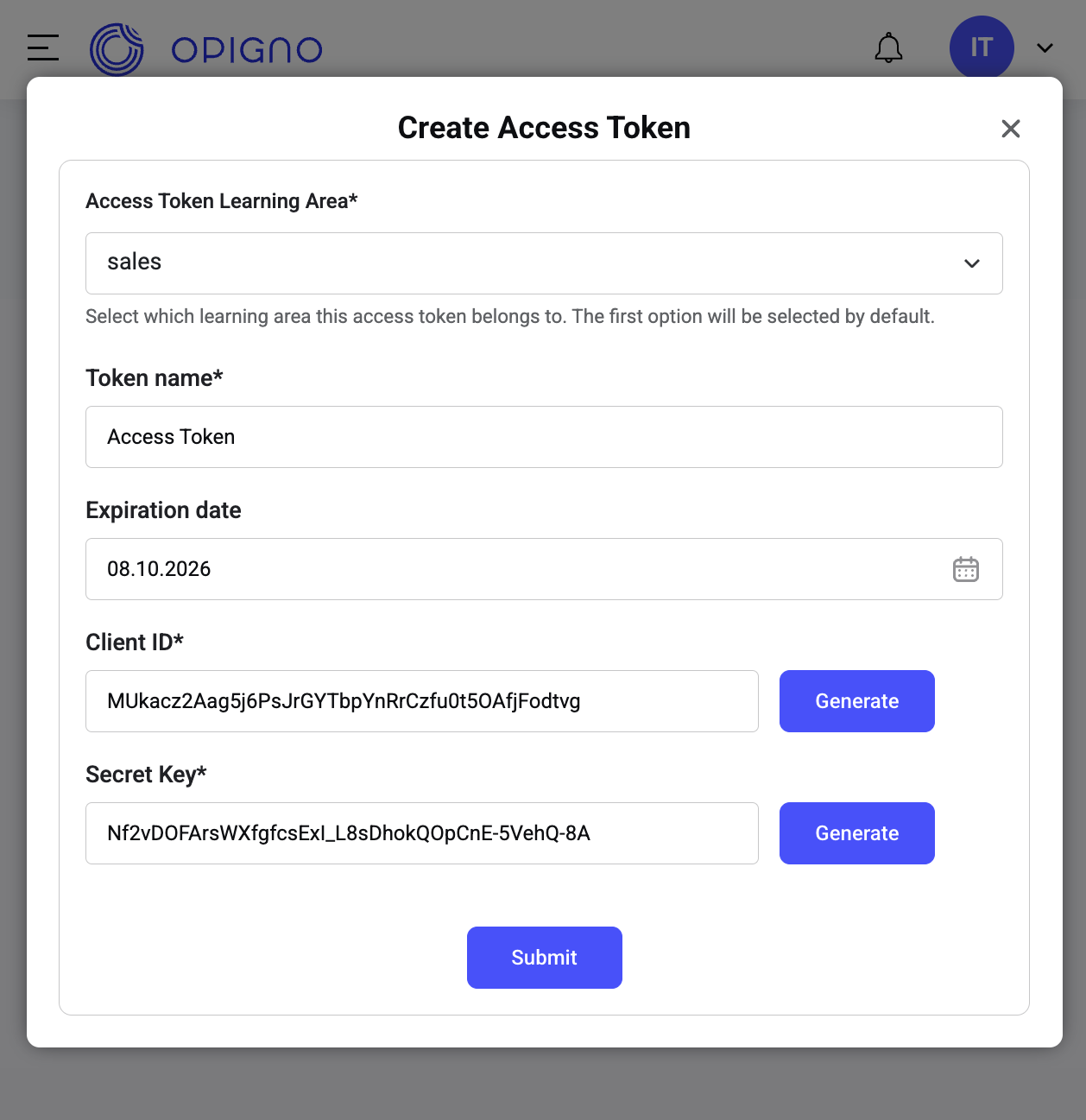
Creating a New Access Token
To add a new access token for API integrations:Configure Token Settings
A modal dialog will appear with the following configuration fields:
Learning Area Selection
Select the learning area this token will be restricted to. The token will only have access to users, trainings, and data within this specific learning area.
Token Name
Enter a descriptive name to identify the token’s purpose. Use clear, meaningful names like:
- “Zapier Integration - Sales Department”
- “HR Management System API”
- “Marketing Automation - Training Sync”
Good naming conventions help you manage multiple tokens effectively, especially when you need to revoke or update them later.
Expiration Period
Set when the token should expire. The default is one year from the creation date.
OAuth2 Credentials
The system automatically generates a unique Client ID when you create the token. This identifier is used in API authentication requests.
The system generates a secure secret key for this token. This value is shown only once during creation.
Generate and Save Credentials
- Review all the configuration settings
- Click Submit to generate the token
- Immediately copy the Client ID and Client Secret
- Store them securely (password manager, secure vault, etc.)
- The new token will appear in the tokens list
After submission, verify that your new token appears in the list with the correct name and expiration date.
Token Security Best Practices
Secure Storage
Secure Storage
Always store credentials securely:
- Use environment variables for production systems
- Store in a password manager or secrets vault
- Never hardcode in application source code
- Keep separate tokens for development and production
.env
Access Control
Access Control
Limit token access appropriately:
- Create separate tokens for each integration
- Assign tokens to specific learning areas only
- Use descriptive names to track usage
- Regularly audit active tokens
- Production:
Zapier Prod - Sales Team - Staging:
Zapier Staging - Sales Team - Development:
Zapier Dev - Testing
Rotation and Expiration
Rotation and Expiration
Implement token rotation policies:
- Set appropriate expiration dates
- Plan token renewal before expiration
- Revoke unused or old tokens
- Update integrations with new credentials promptly
- Production environments: 6-12 months
- Development/testing: 3-6 months
- Temporary integrations: 1-3 months
Monitoring and Auditing
Monitoring and Auditing
Track token usage:
- Regularly review the tokens list
- Monitor expiration dates
- Remove tokens for decommissioned integrations
- Document which systems use which tokens
Managing Existing Tokens
Revoking a Token
If you need to immediately disable a token:Revoke Access
- Click the Revoke action button for that token
- Confirm the revocation when prompted
- The token is immediately invalidated
When to Revoke Tokens
You should revoke tokens when:- The token has been compromised or exposed
- The integration is no longer needed
- An employee with access has left the organization
- You’re replacing it with a new token
- The learning area assignment needs to change
Troubleshooting
Cannot Create New Token
Cannot Create New Token
Possible causes:
- Insufficient administrator permissions
- No learning areas available in the system
- System configuration issues
- Verify you’re logged in as an administrator
- Check that at least one learning area exists
- Contact your system administrator if issues persist
Lost Client Secret
Lost Client Secret
Problem: The client secret was not saved during token creation.Solution:
The secret cannot be retrieved after the creation dialog closes. You must:
- Revoke the existing token
- Create a new token
- Immediately copy and securely store the new credentials
Token Expired
Token Expired
Problem: API requests fail with authentication errors.Solution:
- Check the expiration date in the tokens list
- Create a new token with the same learning area
- Update your integration with the new credentials
- Revoke the old expired token
Wrong Learning Area Assigned
Wrong Learning Area Assigned
Problem: Token doesn’t have access to needed resources.Solution:
Learning area assignments cannot be changed after creation. You must:
- Create a new token with the correct learning area
- Update your integration to use the new token
- Revoke the old token
This security design ensures clear audit trails and prevents accidental privilege escalation.